

Legacy IAM systems are often used as IT administration tools instead of leveraging them as effective security and risk management solutions. These systems lead to unmitigated access risks, failed audits, increase in access misuse incidents, and loss of confidence in IAM programs. With the increase in attack surfaces, organizations must make the shift in viewing IAM as a critical security control. They should focus on building a risk-aware IAM approach to address security flaws and meet privacy and compliance requirements proactively.
Aujas risk-aware IAM services enhanced enterprise capability to mitigate risks, reduce threats, and ensure continuous compliance by enforces policies need to drive business processes. The service intent is to transform legacy IAM solutions to make them risk-aware. Transformation also includes establishing relevant policies and procedures to drive risk-based authentication methods and ensure the right user access.
Read the Risk-Aware IAM Whitepaper
Risk-aware IAM is a crucial imperative for businesses while adopting newer technologies to sustain a competitive edge and deliver better value to customers. When organizations grow, their infrastructure is bound to scale and can have diverse users and access points. They want greater agility in securing user access and credentials to reduce operational complexity and ensure compliance.
Aujas offers services and solutions for organizations of various size and scale enabling them to accommodate the dynamic growth of user access and identities.
Applicable Industry Segment
Benefits
Deliverables
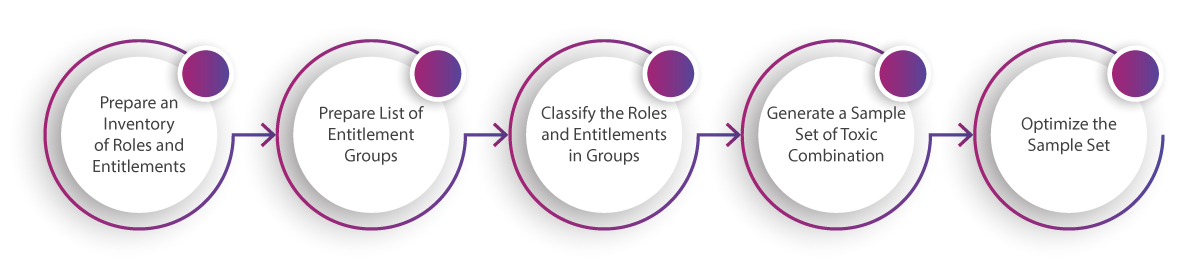
Aujas SoD modeling solution helps businesses through a built-in list of toxic combinations to meet security compliance needs. It also supports multiple use cases such as:
Aujas Risk-aware IAM services can enable you to deploy transformative solutions which can strengthen access governance and are scalable to your process and business needs.
Copyrights © 2025 All Rights Reserved by Aujas.