

In the ever-evolving digital landscape, adopting a traditional approach to IT security is simply not adequate. It cannot safeguard your organizational assets and data fully. Furthermore, with remote workforces, protecting sensitive business information across a distributed geography has become the need of the hour. While many enterprises recognize these shifts, they often lack the expertise, experience, and resources to effectively address these modern security challenges. This prompts an important question: How do you manage the growing threats targeting your IT ecosystem daily?
This is where Aujas Cybersecurity's managed detection and response (MDR) services step in. Our team of experts is tightly integrated with our threat hunters, which allows us to quickly identify and respond to threats. We use this knowledge to constantly evolve the security use cases for anomaly detection and to utilize the NIST framework for incident response and recovery.


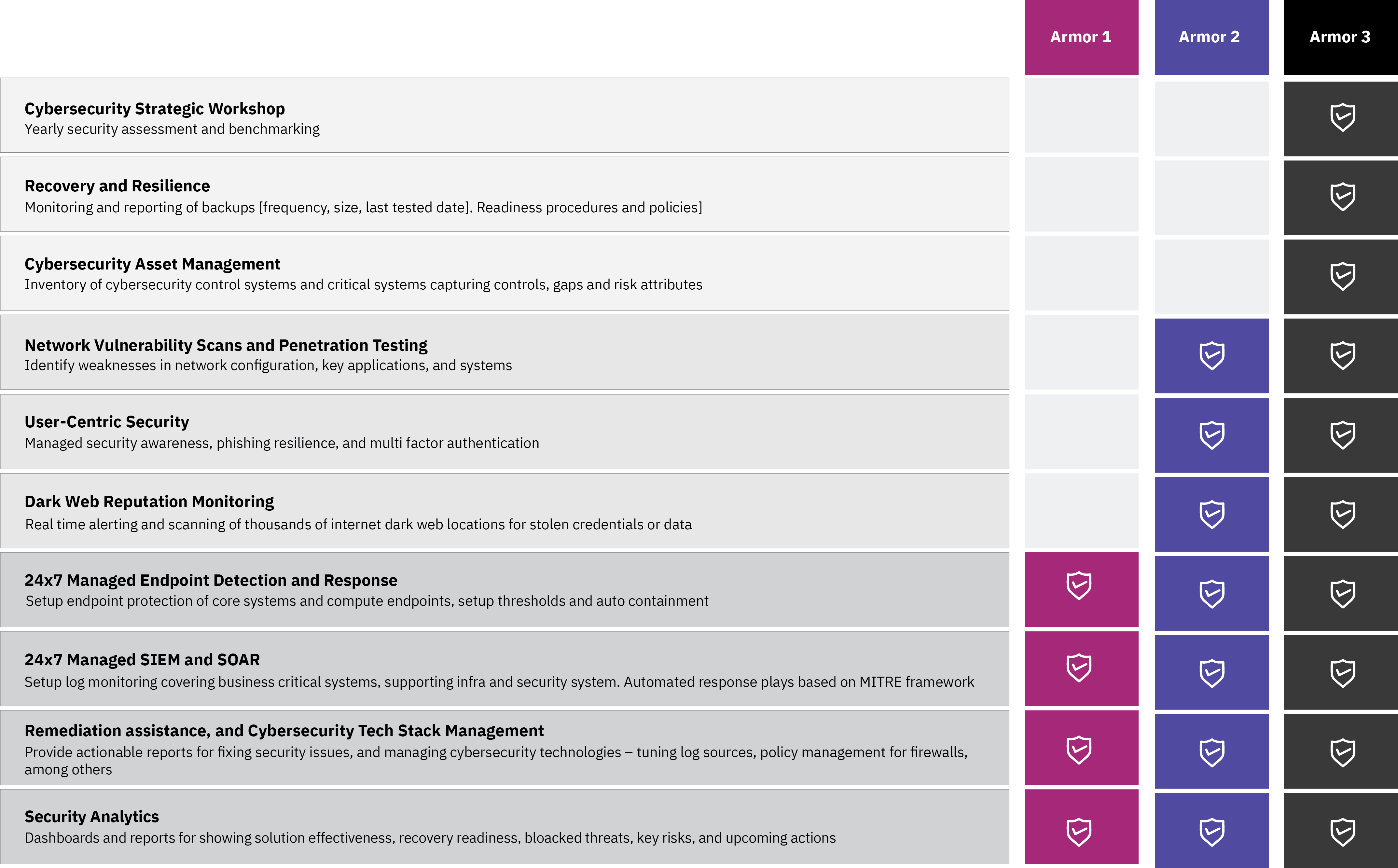

Mitigate risks and safeguard your IT infrastructure against unauthorized access with centralized log management, proactive threat detection, automated incident response, and risk monitoring.
KNOW MORE
Meet regulatory requirements by predicting, detecting, and neutralizing threats ahead of time with advanced security operations, customized controls, strategic threat intelligence, and threat hunting provided by an advanced Security Operation Center (SOC).
KNOW MORE
Counter DDoS attacks, zero-day vulnerabilities, and phishing campaigns with a proactive strategy combining threat intelligence, strategic threat hunting, and forensics.
KNOW MORE
Counter manual tasks, siloed teams, and delayed remediations with SOAR platforms. By integrating security solutions, utilizing threat intelligence, and implementing AI-driven threat detection, SOAR brings down the time required to identify and respond to threats, enhancing collaboration, simplifying workflows, and providing a holistic view of security events.
KNOW MORE
Aujas MDR services safeguard global businesses, shielding their digital ecosystem and assets from evolving threats. This coffee-table e-book highlights our success stories spanning diverse industries.
READ MORE

Know how XDR services can help you overcome security obstacles and mitigate threats at scale.
READ MORECopyrights © 2025 All Rights Reserved by Aujas.