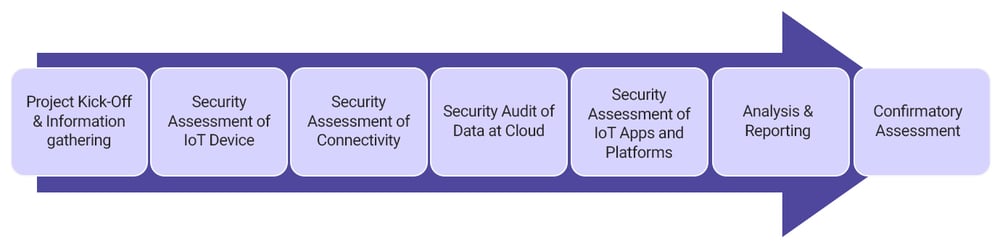
The engagement focus is to mature IoT implementation, processes, controls, and enhance defensive capabilities. IoT security assessments are done in multiple phases by creating scenarios for every interconnected infrastructural asset and through exhaustive checks for every component under test.
Implement secure booting
To encrypt data at rest and in transit between IoT edge devices and back-end systems using standard cryptographic algorithms, ensure data integrity, and prevent data sniffing by malicious entities.
Establish strong encryption mechanism
Build access control mechanisms in operating systems to limit access to device components for authorized personnel.
Maintain role-based access
Enable role-based access for devices by avoiding weak or default credentials.
Change default credentials
Update IoT devices with latest firmware and patches to fix known vulnerabilities.
Keep devices up to date
Authenticate connected devices through device id or a device-specific identifier.
Ensure proper firewall/IPS configuration and network security
Establish device firewall or deep packet inspection capability to control traffic intended for specific network nodes. Monitor inbound ports and ensure they are in a closed state when not in use.
Device status monitoring
Continuously monitor device status (online/offline/all unusual activities) across IoT networks.
Secure provisioning of IoT Devices
Check and certify IoT devices before connecting them to the home or industrial networks.







