

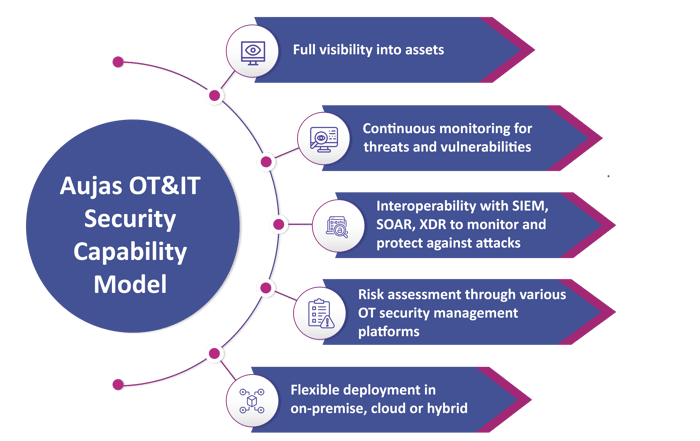
The technological integration of IT&OT networks due to digital transformation leverages data and analytics to provide innovative capabilities, interconnected systems, and streamlined efficiencies. This convergence has also expanded the attack surface leading to new risks. Digital success will depend more on robust security strategies and approaches as industrial connectedness is bound to proliferate exponentially. Be it discovering existing security weaknesses or foreseeing future risks; enterprises feel the need to have next-gen proactive security solutions and capabilities to ensure total visibility & enable risk management for strengthening their ability to combat complex attacks.
Lack of OT systems visibility and continuous monitoring can put the entire OT ecosystem at risk of operational breakdown. Security incidents can happen due to the inability to know vulnerabilities, misconfigurations, and root-cause of incidents.
Unauthorized or incorrect changes can cause misconfigurations in ICS/OT systems, leading to compliance violations posing a risk to the operational stability, safety, and security of these systems.
Systems might get compromised by unauthorized or incorrectly configured firmware or hardware by employees or external personnel. Employees can (unintentionally) install malware through phishing emails or insert USB devices into their IT/OT systems.
Internet exposed OT assets or infected IT systems can pose severe malware and ransomware threats to the OT environment, potentially causing production downtime, loss of sensitive intellectual property, environmental incidents etc.
OT Firewalls Review
OT Network Architecture Review
Security Risks & Gaps, Regulatory Compliance Audit, and Assessment Services
Continuous Threat Management Services
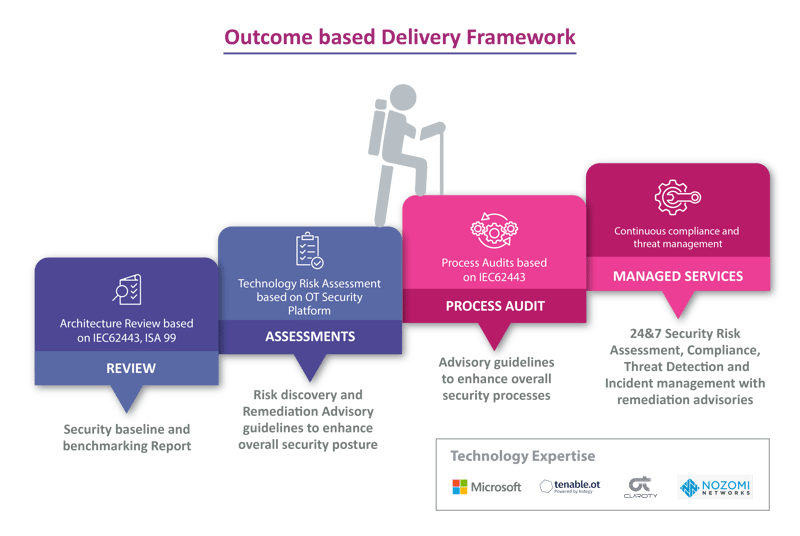
Leading cement manufacturing company in India with an installed capacity of 100+ million tons per annum having multiple manufacturing plants across the globe has initiated an OT security program to secure OT devices and underlying infrastructure. The program included OT devices & infrastructure security, security architecture review, security assessments, and process audits.
The client wanted to assess the current security posture of their OT devices, infrastructure, and processes. Aujas team helped the client to evaluate the current security posture through the below services:
The team used IEC62443/ISA 99 standards to perform these activities and uncovered security risks in OT devices and underlying infrastructure. Aujas’s outcome-based security framework helped the client enhance security processes, securing OT devices and infrastructure through remediation of reported vulnerabilities.
OT Security Assessment
OT Architecture Review
OT Firewall Review
Copyrights © 2025 All Rights Reserved by Aujas.