

Organizations that design and implement IAM programs should comply with security regulations such as SOX, GLBA, NYDFS, SAMA, and DSCI.
By meeting these standards, organizations can establish data access controls and mitigate access risks. Protecting identity and access is a business imperative to reduce data leak risks and can secure information assets even when data access points proliferate.
Aujas Identity Governance Fast Track is a bundled solution offering which can ensure a strong foundation for enterprise IAM initiatives. This solution can drastically cut planning and deployment times for initial IAM deployments.
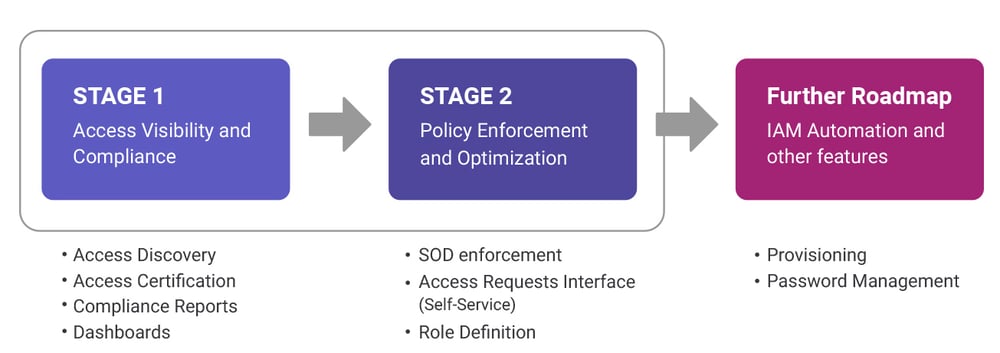
Aujas provides a fast track two-staged approach to achieve access & identity governance goals. This approach provides a modular and flexible method for building the very foundation of a robust and secure IAM program. The approach is also extendable to IAM provisioning, automation, and other operational functionalities as and when required.
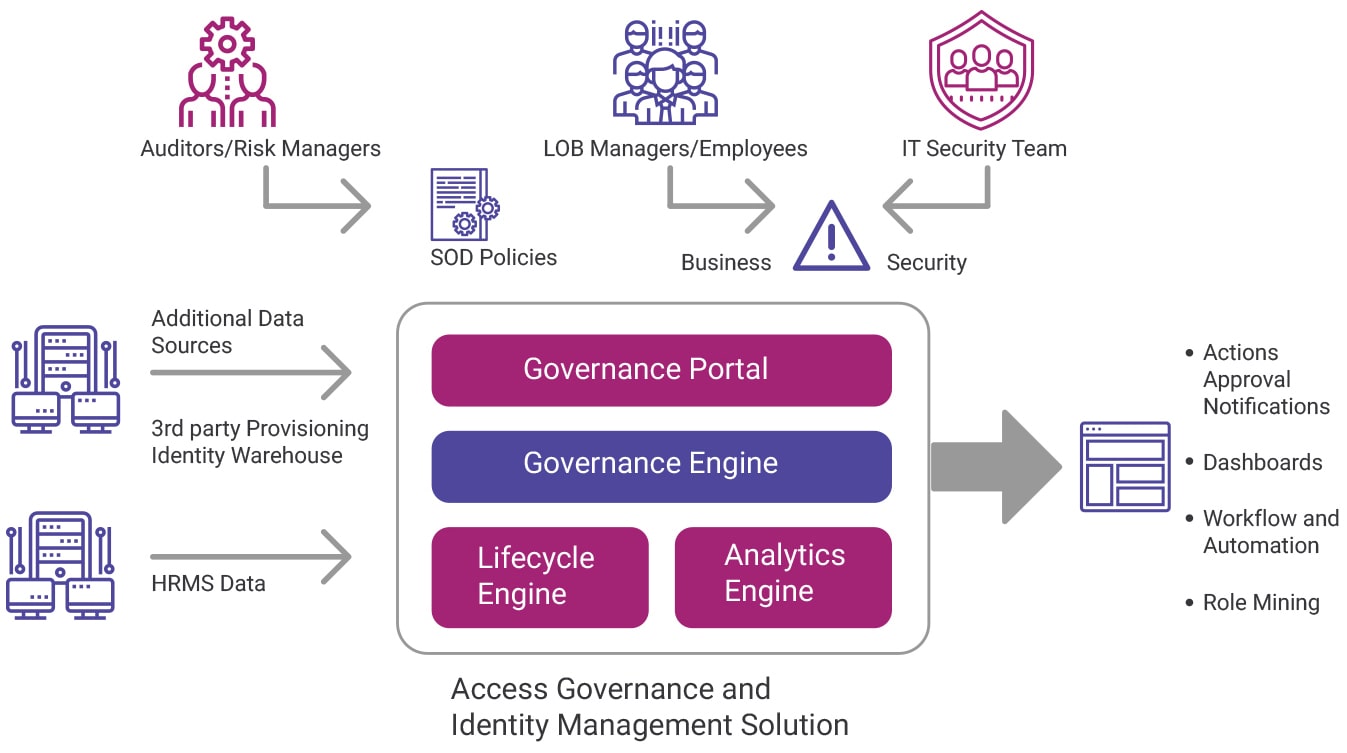
The access governance solution has advanced capabilities to drive access governance and identity lifecycle management needs. The governance engine correlates user data and organization’s policies for role assignment, consolidates user access and can compute policy violations. The governance portal also has an intuitive, business-focused interface. Along with access governance, the solution has automation and role mining capabilities offered through the identify lifecycle module.
We have perfected the art of rapidly deploying IAM solutions by leveraging a range of accelerators and automation frameworks. Our experts can collaborate with you and quickly focus on the relevant areas needed to build a strong IAM foundation. This includes ensuring data protection, privacy governance, and legislative compliance and meeting customer expectations.
Copyrights © 2025 All Rights Reserved by Aujas.