

Organizations are waging an ongoing war with cyber attackers. Cyberattacks have become more complex and harder to detect. Though vulnerability scans and penetration tests are used to assess risks, they are inadequate to test the resilience against the growing threat of multiple attack vectors.
There are also considerable investments to implement security controls, ensure regular audits, protect crown jewel assets, drive non-intrusive and intrusive exercises, and red team-blue team exercises. Despite all these, organizational breach trends are seeing an upward trend. The answer is simple, and the issue is not in the approach, but in the gaps that exist such as:
Organizations are vulnerable to attacks despite having the latest security controls and process, hackers are on the prowl, and they can capitalize on human errors such as misconfigurations, shadow IT, and lack of security awareness. They also use genuine tools and user actions to invade networks and target assets.
Aujas, with its advanced Breach & Attack Simulation (BAS) platform, can help you in evaluating your organization’s readiness to take on cyber threats.
|
Advantages
|
Five Core capabilities
|
|
Differentiators
|
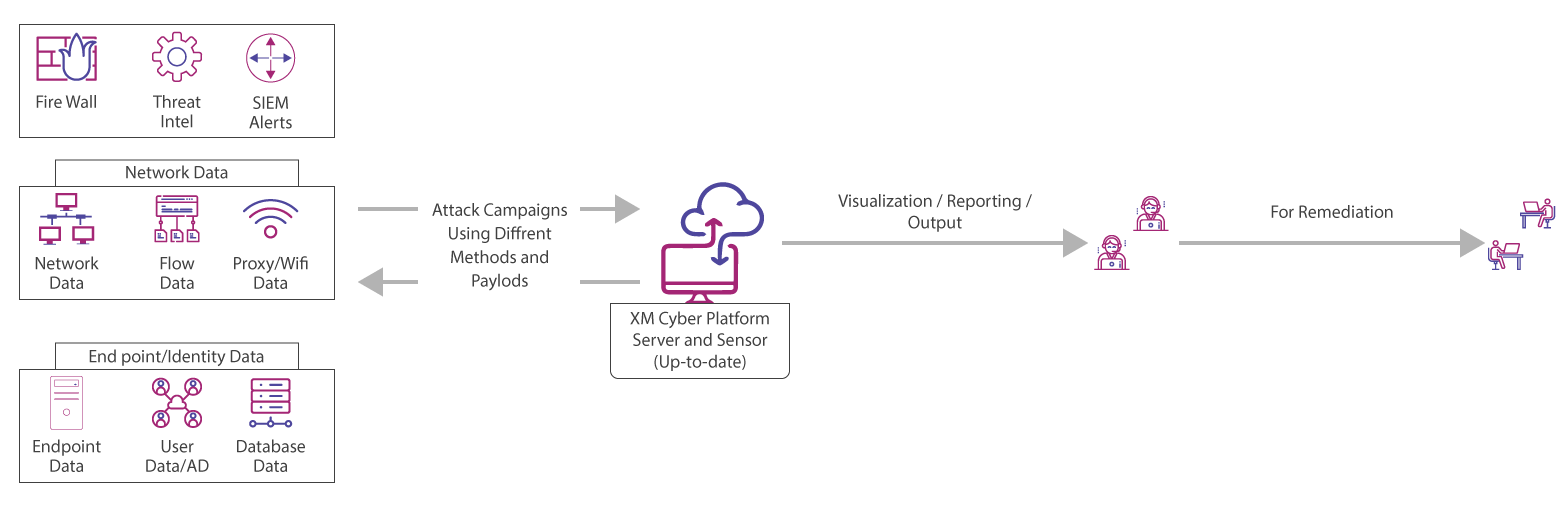
Aujas breach and attack simulation platform can simulate, validate, and remediate attackers’ paths to your critical assets. The platform’s automated purple teaming aligns red and blue teams to provide a full realistic APT experience and prioritized remediations. By addressing real behaviours and exploits, the platform aligns a full spectrum of attack scenarios to your organization’s network. Simulated attacks are then executed to expose blind spots using advanced attack techniques. These attacks are carried out without affecting network availability and user experience.
The Way Platform Works

Our purpose is to provide you with an ultimate APT simulation & remediation platform, which can act as a fully automated purple team. You can leverage the platform to continuously identify all attack paths to their critical assets and receive prioritized actionable remediations.
Aujas can offer you the industry leading, automated, and scalable cybersecurity platform to detect advanced persistent threats. The simulation platform is highly reliable and acts like a real hacker. It has automated processes to find paths used by APT hackers continuously while providing remediation measures.
Platform highlights:
Copyrights © 2025 All Rights Reserved by Aujas.