

Multiple risks can creep in when you build a solution or product across diverse environments. Mitigating these risks can get complicated if they get recognized during the later stages of a development cycle. Threat hunting can help businesses quickly identify and plan risk mitigation efforts in their ecosystem from the beginning of the development cycle.
Threat hunting is a security-based analysis, and its benefits include:
We provide you through the visibility of various risks underlying in any solution and assess it based on business criticality. Our threat modeling services enable you to have a holistic set of controls in place, these controls can help in enforcing mitigations well ahead of the stipulated time.
The engagement focus is to mature security systems, processes, and enhance defensive capabilities by assessing the controls in place.
We use a four-step approach to perform the exercise:
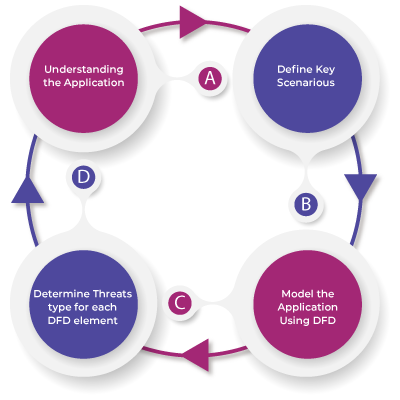
Sophisticated cyber-attacks are posing constant challenges even to those enterprises claiming to be highly evolved security technology bastions. Be it a program, platform or application, there is enough scope for a variety of security breaches, attack vectors, exploits, and malware intrusions.
Our customized range of offerings can enable your data security initiatives, this includes, assessing your security posture, prevent network compromises, and threat intelligence services.
Our expertise can help you to:
Copyrights © 2025 All Rights Reserved by Aujas.