

Enterprises leverage multiple technology stacks during their digital journey. A digital universe generates zettabytes of sensitive data, attracting a hacker’s attention. Employees have begun to access data, servers, and application assets through hybridized cloud environments. They are accessing corporate IT environments remotely and through various devices, expanding the attack surface. This rapid change in access can result in colossal security risks.
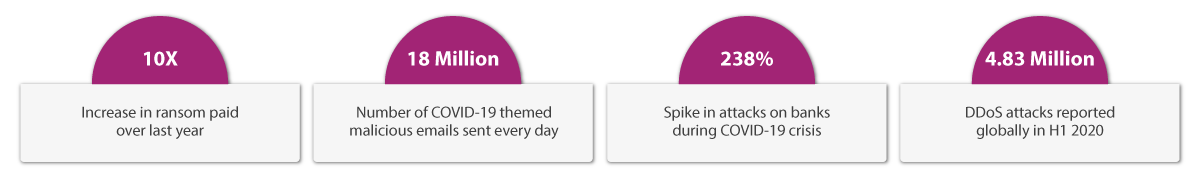
Here are a few recent examples where millions of dollars got swindled due to cyber-attacks.
Aujas has partnered with Microsoft to offer security services consisting of Azure Sentinel, Azure Information Protection, and Microsoft Defender Advanced Threat Protection. Aujas leverages Microsoft’s leading technology platforms to provide robust incident response and managed security services.
Aujas provides comprehensive threat management lifecycle support by using Azure Sentinel through design, build, and managed services.
Azure Information Protection (AIP) is a cloud-based solution that enables organizations to discover, classify, and protect documents and emails by applying labels to content.
Microsoft Defender for endpoints is a comprehensive, cloud-delivered endpoint security solution having multiple features.
Aujas has the expertise and experience in defending the most critical security workloads for large scale security projects across industry verticals. Aujas has successfully developed and built a comprehensive 360 degree Managed Detection and Response (MDR) offering that enables organizations to swiftly act to cyber threats by reducing false positives. The offering also strengthens the security posture through threat intelligence, threat hunting, security monitoring, attack simulations, incident monitoring, incident analysis, and response.
By joining hands with Microsoft, Aujas can offer next-gen integrated security solutions to provide 24x7 cyber defenses for protecting every enterprise asset.
1. Highly Experienced Security Professionals
A core team of certified professionals with multi-disciplinary security expertise in SecOps, security controls, security engineering risk management, and SIEM (Security Information and Event Management).
2. Microsoft Security Center of Excellence
Comprehensive Next-Gen SOC services including Managed SIEM, EDR, analytics, threat hunting, threat intelligence, SecOps, and SOAR services.
3. Aujas Cyber Defense Center (CDC)
Aujas offers CDC services through a 360-degree MDR approach. The approach reflects Aujas’ ability to provide security across the entire enterprise spectrum, including on-premise infrastructure, cloud, and virtual environments.
Ready to get started?
we're here to help.
Engage with us so we can understand your needs and provide the right solutions to help you fulfill your security goals.
Copyrights © 2025 All Rights Reserved by Aujas.