

Aujas can design and manage large application security programs from the requirements gathering phase to final delivery. Application program management services can help you build secure applications through architecture risk analysis, threat modelling, and provide security coding guidelines for your team to mitigate flaws in the early stages of development. Once complete, the final deliverable undergoes a series of penetration tests to make it more robust and secure.
Aujas offers program management services to accelerate application security assessments and drive agility to deliver reliable, secure applications that meet global compliance standards. Our experts can help you establish a roadmap consisting of processes, metrics, and best practices needed to scale your application security program and achieve your delivery goals.
Program management services include:
Aujas security management process involves an active analysis of the application for any potential vulnerabilities due to improper configuration, hardware or software flaws, operational weaknesses process, or technical counter measures. The analysis is made from a potential attacker’s perspective and can involve active exploitation of security vulnerabilities. Our teams use industry best practices & methodologies such as OWASP, SANS 25, OSSTMM, & NIST to drive security testing methodologies.
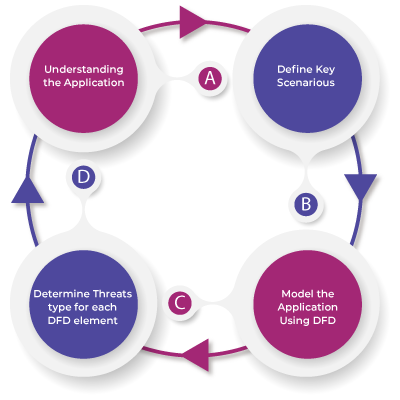
Aujas Application Security Program Management Overview
.png?width=653&name=Static-Application-ST-(SAST).png)
.png?width=946&name=Dynamic-Application-ST-(DAST).png)
Aujas security program management services can help you optimally plan, build and run application assessment programs customized to your business needs. Our experts have extensive knowledge and skills to sustain large scale security program management initiatives while driving them through standardized processes and metrics.
Our service advantages include:
Copyrights © 2025 All Rights Reserved by Aujas.